Multifactor Authentication
What is it and why do we need it?
MFA encompassing 2FA, is an electronic authentication method in which a user is granted access to a website or application only after successful presenting two or more pieces of evidence (factors) to an authentication mechanism: knowledge (something only the user knows), possession(something only the user has), and inherence (something only the user is).
Why do we need multifactor authentication?
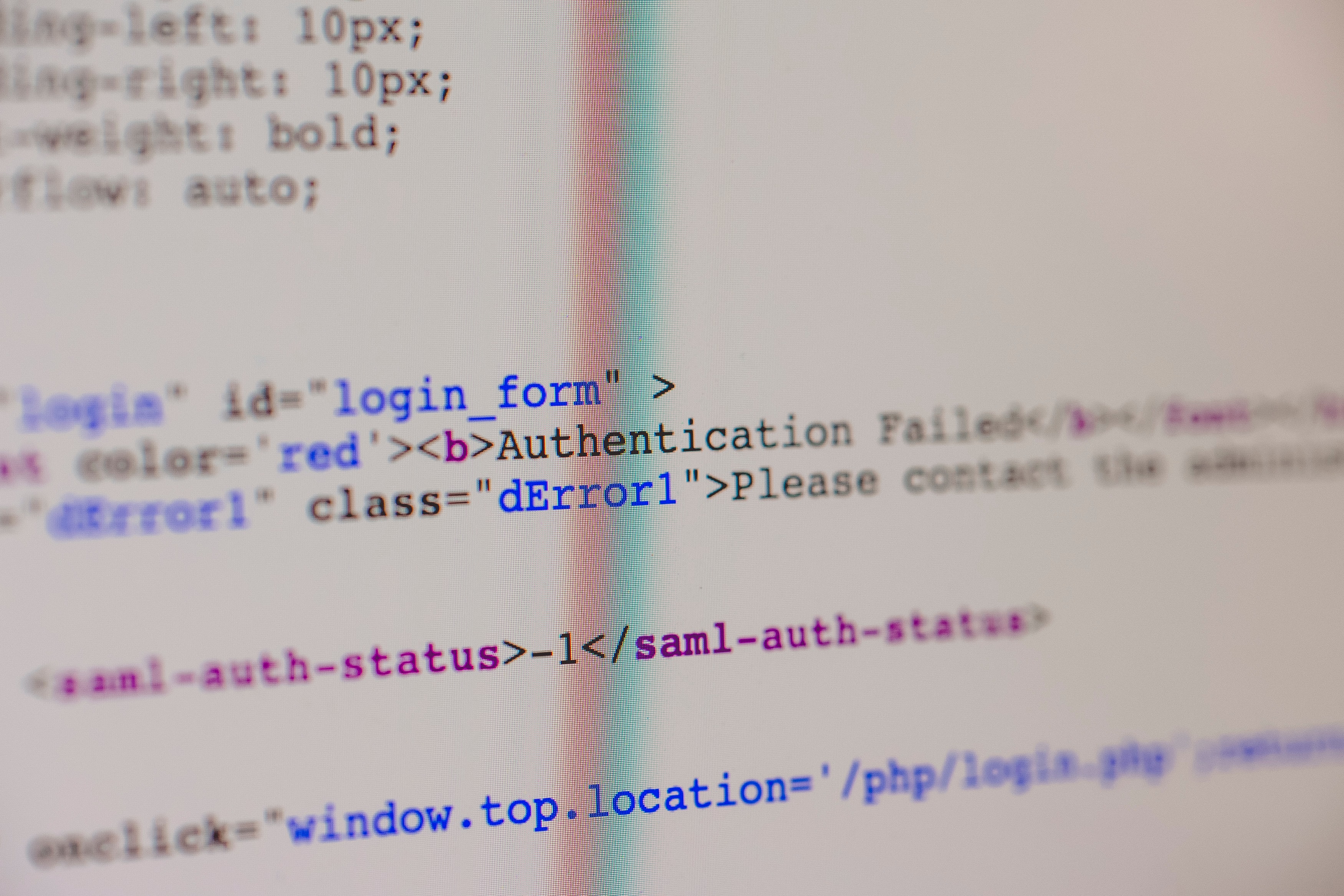
This protects the user from an unknown person trying to access their data.A third-party authenticator
(TPA) app enables two-factor authentication, usually by showing a randomly generated and constantly refreshing
code to use for authentication. The user has to provide information by which he is known to a system before being
let into the system, these are called factors.
The factors include:
i.Something the user has: Some physical object in the possession of the user, such as a security token (USB stick),
a bank card, a key, etc.
ii.Something the user knows: Certain knowledge only known to the user, such as a password
iii.Something the user is: Some physical characteristic of the user (biometrics), such as a fingerprint, voice, pattern
in key press intervals.
iv.Somewhere the user is: Some connection to a specific computer network or using a GPS
How is it implemented?
Many multi-factor authentication products require users to deploy client software to make multi-factor authentication systems work. Some vendors have created separate installation packages for network login, Web access credentials and VPN connection credentials. A third-party authenticator app enables two factor authentication in a different way, usually by showing a randomly generated and constantly refreshing code which the user can use, rather than sending an SMS or using another method. A big benefit of these apps is that they continue to work even without an internet connection.
Where is it applied?
A good example of two-factor authentication is the withdrawing of money in ATM; only the correct combination of a back card and a PIN allows the transaction to be carried out.Another example is to supplement a user-controlled password with a one-time password (OTP) or code generated or received by an authenticator that only the user possesses.Examples of third-party authenticator apps include Google Authenticator, Authy and Microsoft Authenticator; some password managers such as LastPass off the service as well.
What are the types of Multifactor Authentication
i.Knowledge
Knowledge factors are the most commonly used form of authentication. In this form, the user is required to prove knowledge of a secret in order
to authenticate. A password is secret word or a string of characters that is used for user authentication. Is the most used method. Personal identification
number (PIN)
ii.Possession
Possession factors (“something only the user has”) have been used for authentication for centuries, in the form of a key to a lock. The key embodies a secret
which is shared between the lock and the key.A software token is a type of two-factor authentication security device that may be used to authorize the use of
computer services.
iii.Inherent
These are factors associated with the user, and are usually biometric methods, including fingerprint, face, voice, or iris recognition.
iv.Location
The physical location of the user is used. While hard wired to the corporate network, a user could be allowed to login using only a pin code.
Microcontrollers and Microprocessors
Difference between microcontroller and microprocessors
A microcontroller is a chip optimized to control electronic devices. It is stored in a single integrated circuit which is dedicated to performing a particular task and execute one specific application. It is specially designed circuits for embedded applications and is widely used in automatically controlled electronic devices. It contains memory, processor, and programmable I/O. A microprocessor is a controlling unit of a micro-computer wrapped inside a small chip. It performs Arithmetic Logical Unit (ALU) operations and communicates with the other devices connected with it. It is a single integrated circuit in which several functions are combined.
